The move towards smaller transistors brought about deep changes in modern hardware. Performance and energy efficiency increased. But there is an insidious negative to this trend towards smaller processes: while transistor size has decreased, the cost of processor fabrication plants has steadily increased due to the higher complexities involved. By 2020, setting up a fabrication plant may require an upfront investment of 20 billion dollars. Given this monumental cost, most companies outsource fabrication. While this makes sound economic sense, it opens the hardware manufacturing process to a new pernicious attack.
Malicious instructions
Even if we assume that the original designer of the hardware chip is trusted and has introduced no backdoors (malicious instructions hidden from the user’s view) into the system, there is now another trusted entity in the production sequence – the third-party fabrication plant. These fabrication plants are often in different countries with varying degrees of oversight and regulatory pressure, thus increasing the chances of foul play.
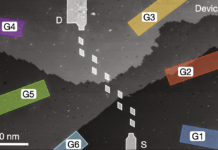
Researchers at the University of Michigan have exploited this newly introduced trust point to execute an attack that results in an undetectable hardware backdoors. The novelty lies in the exploitation of the analog properties of digital circuits to create the backdoor. The core idea of the attack is simple: using the open spaces between wires in an already laid-out circuit, the attacker places a circuit that siphons charge from nearby wires. Once enough charge has been siphoned, the attack circuit is triggered. The circuit is placed in such a way that it is only triggered upon the execution of a specific set of instructions: the perfect recipe for a remote attack with no physical access requirements.
Phantom attacks
Since the circuit is placed post-routing, it is undetectable by functional verification performed on the hardware description language. Moreover, since the circuit is only triggered on the execution of very specific (and highly unlikely) instructions, it is also invisible to all known side channel defenses. Lastly, the attack circuit can be as small as a single gate, thus making it nearly impossible to detect even by scanning using an electron microscope.
So is all hope lost? Not quite. While it is true that there are no existing defense mechanisms that can reliably thwart such a backdoor, the researchers do go on to give ideas for future directions of research. They envision a system where a set of trusted processors monitor untrusted processors to observe any deviance from specified behavior. However, such a system is inherently not cost effective and there also exists the open question of how one would obtain the set of “trusted processors”. Until these questions have been answered, it would behoove security researchers to keep in mind that the hardware they are using might not be as trustworthy as the schematics may make them seem.
Sources:
Yang, Kaiyuan, et al. “A2: Analog malicious hardware.” Security and Privacy (SP), 2016 IEEE Symposium on. IEEE, 2016.